Google Security Vulnerabilities and Updates
Security self-reporting is a good thing
It has definitely been a rough couple of weeks for Google, at least in terms of security nightmares. Last week Google notified people like myself that the Bluetooth Low Energy (BLE) Titan Security key had a manufacturing flaw that could allow someone to intercept the pairing process.
Here's what Google emailed us:
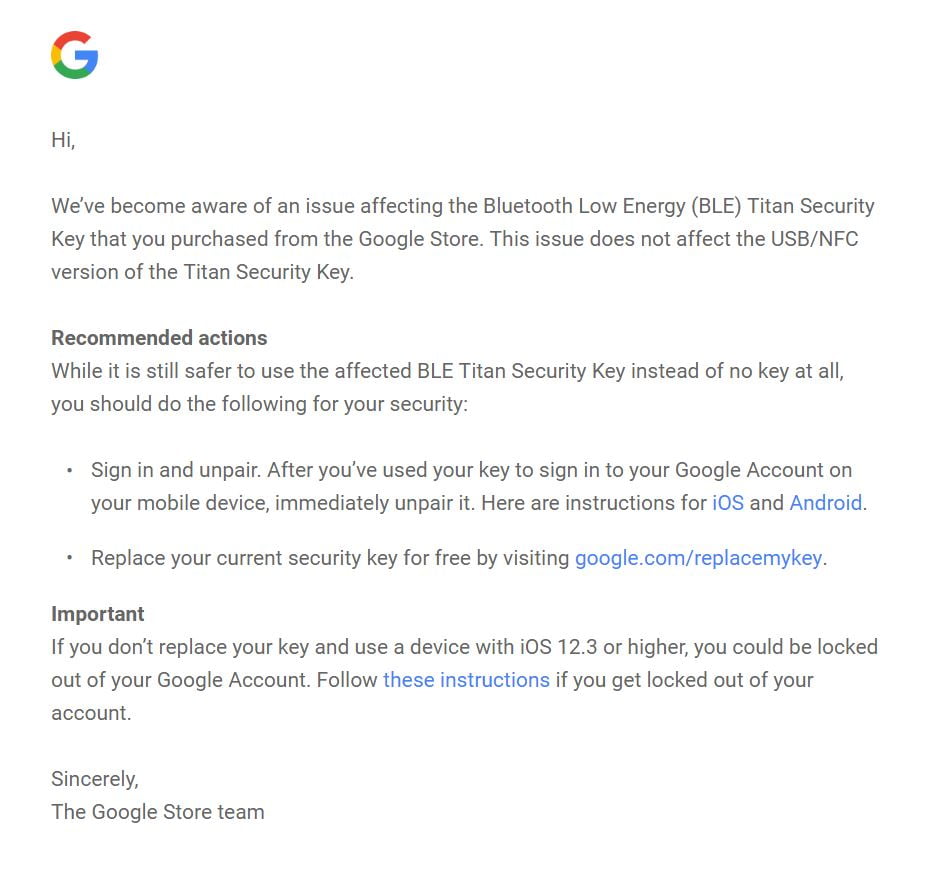
Hi,
We’ve become aware of an issue affecting the Bluetooth Low Energy (BLE) Titan Security Key that you purchased from the Google Store. This issue does not affect the USB/NFC version of the Titan Security Key.
Recommended actions
While it is still safer to use the affected BLE Titan Security Key instead of no key at all, you should do the following for your security:
• Sign in and unpair. After you’ve used your key to sign in to your Google Account on your mobile device, immediately unpair it. Here are instructions for iOS and Android.
• Replace your current security key for free by visiting google.com/replacemykey.
Important
If you don’t replace your key and use a device with iOS 12.3 or higher, you could be locked out of your Google Account. Follow these instructions if you get locked out of your account.
Sincerely,
The Google Store team
This isn't really new-news
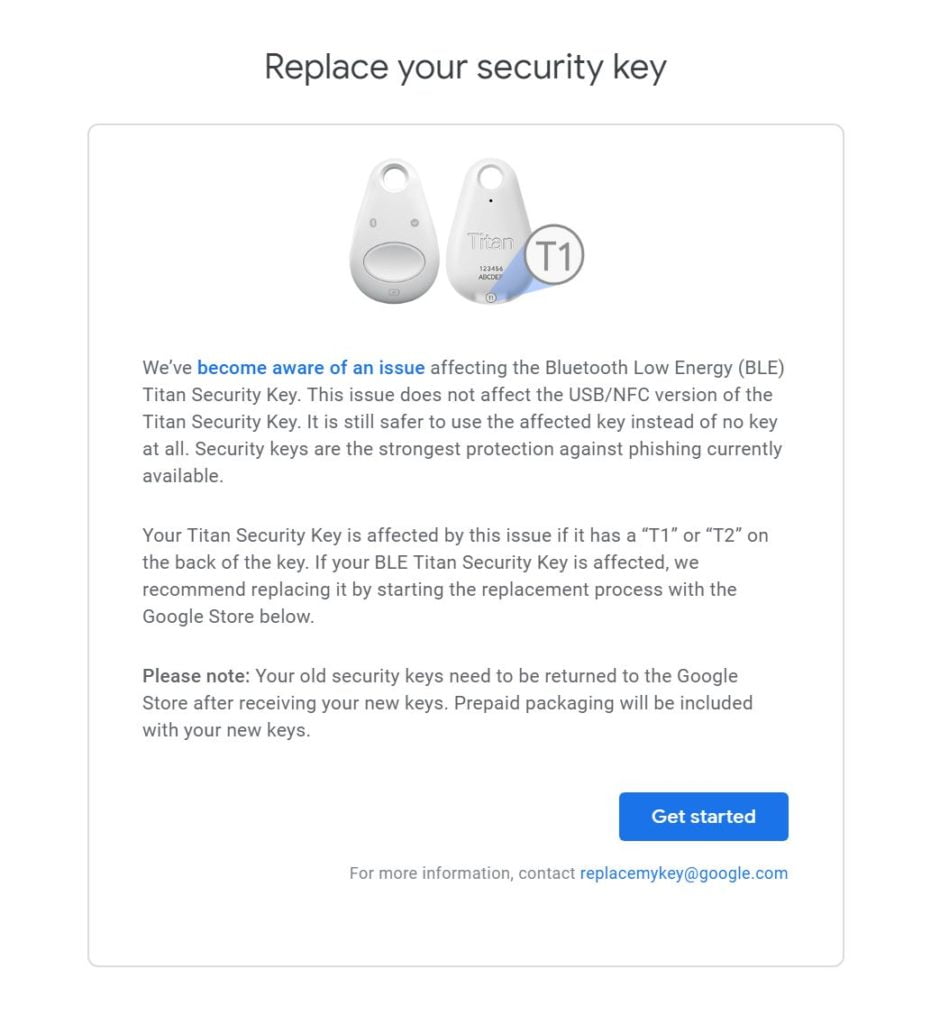
Back in January when I was sent my Titan Security Key Bundle by Google, I noted that it was troubling that the 2 keys were made by 2 different manufacturers. This isn't inherently problematic as a lot of OEM's outsource their parts and manufacturing. What was troubling was that the Bluetooth/NFC Titan Security key is made by Chinese company Feitian Technologies which is part of a Chinese Military Alliance. Many security researchers had noted that so long as Feitian hadn't made any modifications to the FIDO Web Authentication API that they should be fine. At that time, Google hadn't acknowledged any potential issues.
Well, it looks like the concerns were well warranted, as they usually are now that Google is allowing replacements of the T1 and T2 labeled keys.
G Suite plain text passwords
Well, apparently Admin generated and Google generated temporary passwords have been stored in plain text for years for G Suite users. This isn't really a huge pressing issue, unless the password the admin generated was not set to be changed by the user upon next sign-in. Google only identified one of our clients as being affected, and it is a user who hasn't ever signed in. Here's what we were sent:
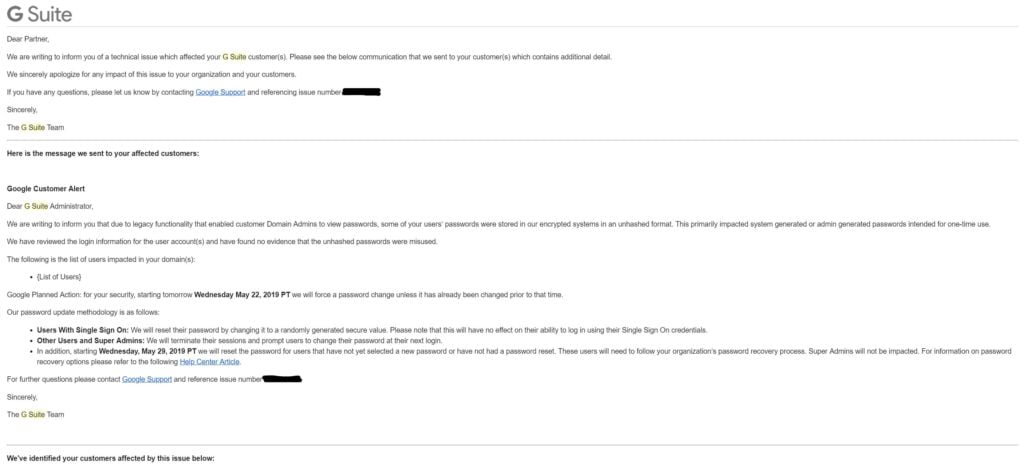
Dear Partner,
We are writing to inform you of a technical issue which affected your G Suite customer(s). Please see the below communication that we sent to your customer(s) which contains additional detail.
We sincerely apologize for any impact of this issue to your organization and your customers.
If you have any questions, please let us know by contacting Google Support and referencing issue number ##########.
Sincerely,
The G Suite Team
Here is the message we sent to your affected customers:
Google Customer Alert
Dear G Suite Administrator,
We are writing to inform you that due to legacy functionality that enabled customer Domain Admins to view passwords, some of your users’ passwords were stored in our encrypted systems in an unhashed format. This primarily impacted system generated or admin generated passwords intended for one-time use.
We have reviewed the login information for the user account(s) and have found no evidence that the unhashed passwords were misused.
The following is the list of users impacted in your domain(s):
List of Users
Google Planned Action: for your security, starting tomorrow Wednesday May 22, 2019 PT we will force a password change unless it has already been changed prior to that time.
Our password update methodology is as follows:
Users With Single Sign On: We will reset their password by changing it to a randomly generated secure value. Please note that this will have no effect on their ability to log in using their Single Sign On credentials.
Other Users and Super Admins: We will terminate their sessions and prompt users to change their password at their next login.
In addition, starting Wednesday, May 29, 2019 PT we will reset the password for users that have not yet selected a new password or have not had a password reset. These users will need to follow your organization’s password recovery process. Super Admins will not be impacted. For information on password recovery options please refer to the following Help Center Article.
For further questions please contact Google Support and reference issue number ##########.
Sincerely,
The G Suite Team
We've identified your customers affected by this issue below:
All-in-all, it's just another day in the tech industry I guess.
Originally Posted to Lemacks Media https://lemacksmedia.com/news/05/22/google-security-vulnerabilities-and-updates/ , by Andrew Lemacks for updates and more content.

Comments
Post a Comment